
- My presentations

Auth with social network:
Download presentation
We think you have liked this presentation. If you wish to download it, please recommend it to your friends in any social system. Share buttons are a little bit lower. Thank you!
Presentation is loading. Please wait.
Data Encryption Standard (DES)
Published by Charleen Allen Modified over 9 years ago
Similar presentations
Presentation on theme: "Data Encryption Standard (DES)"— Presentation transcript:
1 Lecture 3: Secret Key Cryptography Outline concepts DES IDEA AES.

1 CIS 5371 Cryptography 5b. Pseudorandom Objects in Practice Block Ciphers.

Cryptography and Network Security Chapter 3

The Advanced Encryption Standard (AES) Simplified.
Rachana Y. Patil 1 Data Encryption Standard (DES) (DES)

Symmetric Encryption Example: DES Weichao Wang. 2 Overview of the DES A block cipher: – encrypts blocks of 64 bits using a 64 bit key – outputs 64 bits.

Cryptography and Network Security, resuming some notes Dr. M. Sakalli.

Cryptography1 CPSC 3730 Cryptography Chapter 3 DES.

Advanced Encryption Standard(AES) Presented by: Venkata Marella Slide #9-1.

DES 1 Data Encryption Standard DES 2 Data Encryption Standard DES developed in 1970’s Based on IBM Lucifer cipher U.S. government standard DES.
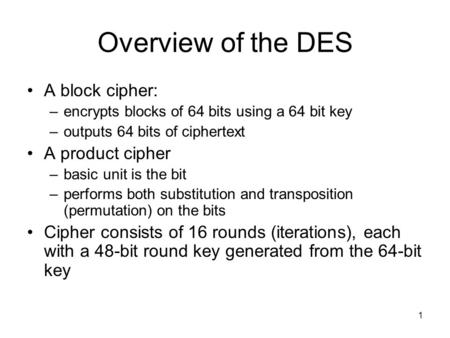
1 Overview of the DES A block cipher: –encrypts blocks of 64 bits using a 64 bit key –outputs 64 bits of ciphertext A product cipher –basic unit is the.

McGraw-Hill©The McGraw-Hill Companies, Inc., Security PART VII.

ICS 454: Principles of Cryptography

CS Network Security Lecture 2 Prof. Katz. 9/7/2000Lecture 2 - Data Encryption2 DES – Data Encryption Standard Private key. Encrypts by series of.

Lecture 23 Symmetric Encryption

Lecture 2.2: Private Key Cryptography II CS 436/636/736 Spring 2012 Nitesh Saxena.

Chapter 3 – Block Ciphers and the Data Encryption Standard

CSE 651: Introduction to Network Security
About project
© 2024 SlidePlayer.com Inc. All rights reserved.

DES - Data Encryption Standard | Data Encryption Standard In Cryptography | Simp
Jul 25, 2021
390 likes | 2.16k Views
In this presentation on DES - Data Encryption Standard, we learn about the origin of the encryption algorithm while understanding the importance of Feistel Ciphers. The steps for encryption and decryption are explained in detail, and we also read about the future of the Data Encryption Standard in cryptography. In the end, we take a look at a live example to further highlight the characteristics of DES encryption.<br><br>Learn more at https://www.simplilearn.com/cyber-security-expert-master-program-training-course
Share Presentation

Presentation Transcript
Today’s Agenda What Is DES? Origin of DES Feistel Ciphers How DES Works Future of DES Live Example
What Is DES?
Click here to watch the video
What Is DES? • Stands for Data Encryption Standard • Symmetric-Key algorithm using block-by-block encryption • Block size is 64 bits and key size is 48 bits • Follows the Feistel Cipher structure Block 1 Block 2 Block n Plaintext Broken down to 64-bit blocks
Origin of DES
Feistel Ciphers
Feistel Ciphers • Block Cipher that is used as a structure for encryption algorithms • Uses substitution and permutation alternately • Based on Shannon Structure from 1945 • Developed by Horst Feistel • Reversing the process can decrypt ciphertext back to plaintext
Feistel Ciphers Plaintext (64-bit) Left Half(32-bit) Right Half(32-bit) + XOR Operation F Encryption Key used here New Left Half New Right Half
Round Function One Half (32-bit) Expansion Box + 48-bit Text Kn 48-bit Key 48-bit Output
Round Function 48-bit Output S-Box XOR’d with the other half of plaintext 32-bit Output
Structure Guidelines • Block size should be a compromise between size and speed
Structure Guidelines • Block size should be a compromise between size and speed • Key size is directly proportional to strength of encryption
Structure Guidelines • Block size should be a compromise between size and speed • Key size is directly proportional to strength of encryption • Higher the number of rounds, tougher it is to crack
Structure Guidelines • Block size should be a compromise between size and speed • Key size is directly proportional to strength of encryption • Higher the number of rounds, tougher it is to crack • Round function should be complex
Structure Guidelines • Block size should be a compromise between size and speed • Key size is directly proportional to strength of encryption • Higher the number of rounds, tougher it is to crack • Round function should be complex • Speed is essential to handle large amounts of data
How DES Works
How DES Works – Key Generation 64-bit Plaintext Initial Permutation K0 Round 1 48-bit key K1 56-bit Cipher Key Round 2 Round-key Generator 48-bit key K15 Round 16 48-bit key Final Permutation 64-bit Ciphertext
How DES Works - Decryption 64-bit Ciphertext Final Permutation K15 Round 16 48-bit key 56-bit Cipher Key K1 Round-key Generator Round 2 48-bit key K0 Round 1 48-bit key 64-bit Plaintext Initial Permutation
Modes of Operation Electronic Codebook Cipher Block Chaining DES Cipher Feedback Block Output Feedback Counter Method
Future of DES
Future of DES • Replaced by AES in 2002 as the world standard for encryption • 56-bit key size easily broken by new generation computers • Withdrawn support for official purposes in 2005 • Triple-DES still allowed for important data till 2030
Live Example
- More by User

Data Encryption Standard
Data Encryption Standard. CS-471/971. Category of Standard : Computer Security. Explanation : The Data Encryption Standard (DES) specifies a FIPS approved cryptographic algorithm as required by FIPS 140-1.
926 views • 38 slides

Data Encryption Standard (DES)
Data Encryption Standard (DES). Bahan Kuliah ke-12 IF5054 Kriptografi. Sejarah. Dikembangkan di IBM pada tahun 1972. Beradsarkan pada algoritma Lucifer yang dibuat oleh Horst Feistel.
793 views • 32 slides
The data encryption standard (DES)
Online Cryptography Course Dan Boneh. Block ciphers. The data encryption standard (DES). Block ciphers: crypto work horse. n bits. n bits. E, D. PT Block. CT Block. Key. k Bits. Canonical examples: 3DES: n= 64 bits, k = 168 bits
568 views • 16 slides

Lect. 7 : Data Encryption Standard
Lect. 7 : Data Encryption Standard . Plaintext block 64 bits. Key 56 bits. DES. Ciphertext block 64 bits. Data Encryption Standard (DES). DES - History 1976 – adopted as a federal standard 1977 – official publication as FIPS PUB 46 1983, 1987, 1993 – recertified for another 5 years.
591 views • 17 slides

Data Encryption Standard (DES). Symmetric Cryptography. C = E(P,K) P = D(C,K) Requirements Given C, the only way to obtain P should be with the knowledge of K Any attempt to attack the cipher should be comparable in complexity to brute-force method
574 views • 27 slides

INCS 741: Cryptography. Data Encryption Standard (DES). Dr. Monther Aldwairi New York Institute of Technology- Amman Campus 10/18/2010. Block Ciphers. Block Ciphers. Stream ciphers process messages a bit or byte at a time when en/decrypting Vigenère Cipher Caeser Cipher
1.15k views • 70 slides

OCHRONA KRYPTOGRAFICZNA Data Encryption Standard – DES Advanced Encryption Standard - AES
OCHRONA KRYPTOGRAFICZNA Data Encryption Standard – DES Advanced Encryption Standard - AES. Transformacje oktalne w binarne. 1 1 0. Transformacje binarne w oktalne. 0 1 1. Teoria idealnej szyfracji. Shannon (1940) – nieskończony klucz, konfuzja i dyfuzja Konfuzja (1)
284 views • 7 slides

DES (Data Encryption Standard) Şifreleme Algoritması
DES (Data Encryption Standard) Şifreleme Algoritması. Başlamak için menülere tıklayın. Simetrik Kriptografi (Şifreleme). DES (Data Encryption Standard). DES Algoritması Nasıl Kırıldı…. S-DES Şifreleme Algoritması. 3 DES Algoritması. Hazırlayan:. Menü.
742 views • 18 slides

Data Encryption Standard. Data Encryption Standard. DES developed in 1970’s Based on IBM Lucifer cipher U.S. government standard DES development was controversial NSA was secretly involved Design process not open Key length was reduced Subtle changes to Lucifer algorithm. DES Numerology.
407 views • 12 slides

Data Encryption Standard (DES). Developed in 1970s for the U.S. Gov’t, intended for use by the public Uses combinations of substitution and transposition (16 cycles) Uses a 64 bit key (8 bits for check digits) to encrypt blocks of 64 bits
329 views • 12 slides

Chủ đề 4: Data Encryption Standard và Advanced Encryption Standard
Chủ đề 4: Data Encryption Standard và Advanced Encryption Standard. ThS. Trần Minh Triết. Nội dung. Data Encryption Standard Advanced Encryption Standard. Mã hóa tích (Product Cipher).
911 views • 55 slides

6 장 . Data Encryption Standard (DES)
6 장 . Data Encryption Standard (DES). 경일대학교 사이버보안학과 김 현 성 교수. 목차. 6.1 개요 6.2 DES 의 구조 6.3 DES 분석 6.4 다중 DES 6.5 DES 의 안전성. 6.1 개요. DES 대칭키 블록암호로 미국 국립기술표준원 (NIST, National Institute of Standards Technology) 에서 공표 이 절의 내용 역사 (History) 개요 ( Overview). 6.1 개요 – 역사.
1.86k views • 65 slides

Data Encryption Standard - DES
DES was developed as a standard for communications and data protection by an IBM research team, in response to a public request for proposals by the NBS - the National Bureau of Standards (which is now known as NIST). Data Encryption Standard - DES. Lecture Plan. Review of Encryption
1.62k views • 63 slides

Data Encryption Standard (DES). Most widely used block cipher in the world Adopted in 1977 by National Bureau Standards (NBS) Encrypts 64-bit data using 56-bit key Has widespread use Has been considerable controversy over its security. DES. Details of A Single Iteration.
2.23k views • 35 slides

DATA ENCRYPTION STANDARD (DES)
DATA ENCRYPTION STANDARD (DES). Outline. History Encryption Key Generation Decryption Attacks On DES DES Cracker Improved Key Size for 2DES,3DES. History. In 1971, IBM developed an algorithm, named LUCIFER which operates on a block of 64 bits , using a 128-bit key.
1.12k views • 48 slides

723 views • 63 slides

Performance Analysis of Data Encryption Standard DES
Information security is becoming much more important in data storage and transmission with the fast progression of digital data exchange in electronic way. Cryptography has come up as a solution which plays a vital role in information security system against malicious attacks. The cryptography is most important aspect of communications security and becoming an important building block for computer security. This security mechanism uses some algorithms to scramble data into unreadable text which can be only being decoded or decrypted by party those possesses the associated key. To protect sent messages that some of the most commonly used cryptography methods with private key based algorithm are LOKI 89, 91, 97 , DES, triple DES, AES, Blowfish, etc. These algorithms also include several computational issues as well as the analysis of DES algorithm. The main features that specify and differentiate one algorithm from another are the ability to the speed of encryption and decryption of the input plain text. This paper analyzes the private key based algorithm DES and LOKI91 by computing index of coincidence IC and time efficiency. Thida Soe | Soe Soe Mon | Khin Aye Thu "Performance Analysis of Data Encryption Standard (DES)" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-3 | Issue-5 , August 2019, URL: https://www.ijtsrd.com/papers/ijtsrd26650.pdf Paper URL: https://www.ijtsrd.com/computer-science/computer-security/26650/performance-analysis-of-data-encryption-standard-des/thida-soe
79 views • 5 slides
- Preferences

DATA ENCRYPTION STANDARD - PowerPoint PPT Presentation

DATA ENCRYPTION STANDARD
Des is an encryption block cipher that encrypts data in 64-bit blocks. ... official description, 'data encryption standard', published january 15, 1977. ... – powerpoint ppt presentation.
- Shirley Ann Fogarty
- Pat OCallaghan
- Karen Waters
- Eoin Cosgrave
- DES was developed by IBM and was endorsed by the US government in 1977 as an official standard.
- DES is an encryption block cipher that encrypts data in 64-bit blocks.
- When in use, both the receiver and the sender must use the same key for encryption and decryption.
- Main Components Algorithm and key
- 64 - bit block of plaintext enters algorithm.
- Split in half, combined with the key and 16 identical rounds are performed on it.
- 64-bit block of ciphertext is produced from the algorithm.
- National Bureau of Standards (NBS) wanted a program to protect computer and communications data .
- IBM developed an algorithm from an old algorithm called Lucifer.
- The response from the public was good yet wary due to the involvement of the NSA.
- Official description, Data Encryption Standard, published January 15, 1977.
- DES is reviewed every 5 years.
- To this day no suitable replacement algorithm has been found.
- DES is expected to have a backdoor in the algorithm.
- There are 64 weak keys and when used for the initial keys can cause security problems.
- There are rumors that a computer has been built which can crack it in 3 hours.
- Multiple DESThe algorithm is applied several times
- Tuchman developed a method known as Triple Encryption with Two Keys (EDE mode)
- Doubling the block length128 vs. 64 bit block pros and cons
- DES The algorithm of choice
- Users include IBM, Motorola and General Electric
- DES based products include mobile radio units and encryption boxes for use with microwave, satellite and other types of communications
- Several cryptographers have brought lawsuits against the U.S Government.
- Between the 1970s and 1990s NSA threatened people with prosecution if they published certain scientific papers
- 1996 saw a decision that no attempts should be made to regulate publications in books or any form of paper .
- On 1/7/98, IBM submitted a new encryption algorithm to NIST for consideration as the AES
- It has a 128-bit key, and can be used in hardware, software and in bandwidth-constrained applications i.e smart cards.
- Although DES is still a strong encryption algorithm NIST is said to be preparing for its eventual replacement.
PowerShow.com is a leading presentation sharing website. It has millions of presentations already uploaded and available with 1,000s more being uploaded by its users every day. Whatever your area of interest, here you’ll be able to find and view presentations you’ll love and possibly download. And, best of all, it is completely free and easy to use.
You might even have a presentation you’d like to share with others. If so, just upload it to PowerShow.com. We’ll convert it to an HTML5 slideshow that includes all the media types you’ve already added: audio, video, music, pictures, animations and transition effects. Then you can share it with your target audience as well as PowerShow.com’s millions of monthly visitors. And, again, it’s all free.
About the Developers
PowerShow.com is brought to you by CrystalGraphics , the award-winning developer and market-leading publisher of rich-media enhancement products for presentations. Our product offerings include millions of PowerPoint templates, diagrams, animated 3D characters and more.

IMAGES
COMMENTS
This document discusses data encryption and digital signatures. It defines encryption as disguising information so that only those with the key can access it. There are two main types of encryption - symmetric which uses the same key for encryption and decryption, and asymmetric which uses different keys.
- DES (Data Encryption Standard) is a symmetric block cipher algorithm that encrypts data in 64-bit blocks using a 56-bit key. It was the first encryption standard adopted by the U.S. government for protecting sensitive unclassified federal government information.
Encryption is a technique that scrambles data to make it unreadable by anyone without access to the decryption key. There are different types of encryption methods, including hashing, symmetric encryption (using a single private key), and asymmetric encryption (using a public and private key pair). Common encryption algorithms include Triple ...
Data Encryption Standard (DES) Most widely used block cipher in the world . Adopted in 1977 by National Bureau Standards (NBS) Encrypts 64-bit data using 56-bit key – A free PowerPoint PPT presentation (displayed as an HTML5 slide show) on PowerShow.com - id: 47752e-MjhiZ.
E N D. Presentation Transcript. DATA ENCRYPTION STANDARD (DES) Outline • History • Encryption • Key Generation • Decryption • Attacks On DES • DES Cracker • Improved Key Size for 2DES,3DES.
Data Encryption Standard CS-471/971. Category of Standard: Computer Security. Explanation: The Data Encryption Standard (DES) specifies a FIPS approved.
Data Encryption Standard (DES) Symmetric Encryption Example: DES Weichao Wang. 2 Overview of the DES A block cipher: – encrypts blocks of 64 bits using a 64 bit key – outputs 64 bits. Cryptography and Network Security, resuming some notes Dr. M. Sakalli.
The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Whether you have daily or monthly meetings, a brilliant presentation is necessary.
In this presentation on DES - Data Encryption Standard, we learn about the origin of the encryption algorithm while understanding the importance of Feistel Ciphers. The steps for encryption and decryption are explained in detail, and we also read about the future of the Data Encryption Standard...
DATA ENCRYPTION STANDARD. Shirley Ann Fogarty ; Pat OCallaghan; Karen Waters ; Eoin Cosgrave; 2 Introduction to DES. DES was developed by IBM and was endorsed by the US government in 1977 as an official standard. DES is an encryption block cipher that encrypts data in 64-bit blocks. When in use, both the receiver and the sender must use the ...